Table of Contents
Introduction
My previous blog post described how to deploy AWS Resources across Regions using Terraform. It explained how Terraform Provider Aliases work and helps with multi-region deployments. Now, I will show you how to deploy AWS resources in multiple AWS Accounts using Aliases. The Terraform Cloud will be used to securely store the AWS credentials (Access Key/Secret Key). The Terraform Provider Aliases are documented here: Terraform Multiple Provider Configurations. Alright, let’s dive right in!
Terraform Cloud
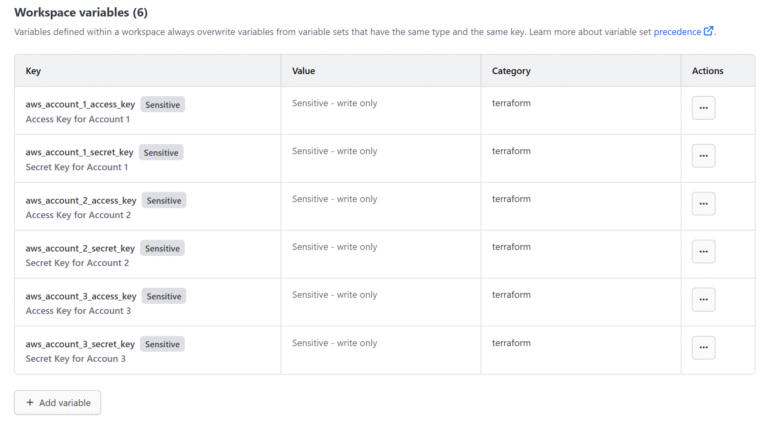
Let’s assume that we have to deploy a couple of AWS VPCs across three different AWS Accounts. What is more, we want to do it using Terraform. We will use long-term credentials: AWS Access Key and Secret Key ( https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html ). Every IAM User owns a different set of Access Key / Secret Key. Those credentials will be kept in the Terraform Cloud Workspace Variables. Tt will allow Terraform to use those credentials and create the AWS resources.
I will create a new Terraform Cloud Workspace. Each AWS Account requires its own Access Key – Secret Key pair. Having three AWS Accounts, we need 3 such pairs (three Access Keys and there Secret keys = six variables in total). Let’s give the variables meaningful names.
Now, let’s jump straight into the code. Please note that I will use the same Module as described in my previous blog article, so most of the code may be familiar to you ( https://cloud-cod.com/index.php/2025/08/05/deploying-aws-resources-in-multiple-regions-using-terraform-provider-aliases/ ).
Module Code
The module (which I store locally as a folder) will create a VPC. The user will have to provide the CIDR range and the Name.
The main.tf file:
resource "aws_vpc" "vpc" {
provider = aws.provider
cidr_block = var.vpc_cidr
tags = {
Name = var.vpc_name
}
}
The variables.tf file:
variable "vpc_cidr" {
type = string
}
variable "vpc_name" {
type = string
}
The versions.tf file:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 6.0"
configuration_aliases = [ aws.provider ] # provider name will be passed to the module
}
}
required_version = ">= 1.2.0"
}
Very important! The usage of the argument called configuration_aliases inside the module allows two things:
- The provider configuration will be passed from the ROOT to the module (and it is the ROOT that will select the Region for the resource)
- The resources inside the module will be allowed to use the provider argument.
Main Code
The root versions.tf file:
terraform {
# please put your backend config here
cloud {
organization = "<your-org>"
workspaces {
name = "<tfc-workspace-name>"
}
}
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 6.0"
}
}
}
The root variables.tf. Please note we need a pair of Access-Ke/Secret-Key variables for every Account.
# Account 1
variable "aws_account_1_access_key" {}
variable "aws_account_1_secret_key" {}
# Account 2
variable "aws_account_2_access_key" {}
variable "aws_account_2_secret_key" {}
# Account 3
variable "aws_account_3_access_key" {}
variable "aws_account_3_secret_key" {}
The root providers.tf file. I define three providers with Aliases. Each provider will be used to create AWS resources in different AWS Account:
provider "aws" {
alias = "account_1"
region = "eu-west-1"
access_key = var.aws_account_1_access_key
secret_key = var.aws_account_1_secret_key
}
provider "aws" {
alias = "account_2"
region = "eu-west-1"
access_key = var.aws_account_2_access_key
secret_key = var.aws_account_2_secret_key
}
provider "aws" {
alias = "account_3"
region = "eu-west-1"
access_key = var.aws_account_3_access_key
secret_key = var.aws_account_3_secret_key
}
The root main.tf file. I create three VPCs by calling my local module three times. Each time I use a different provider alias to deploy resources in different AWS Accounts.
module "vpc-account-1" {
source = "./vpc_module"
vpc_name = "vpc-eu-west-1"
vpc_cidr = "10.80.0.0/16"
providers = {
aws.provider = aws.account_1 # we have to instruct the module what provider to be used
}
}
module "vpc-account-2" {
source = "./vpc_module"
vpc_name = "vpc-eu-west-1"
vpc_cidr = "10.80.0.0/16"
providers = {
aws.provider = aws.account_2 # we have to instruct the module what provider to be used
}
}
module "vpc-account-3" {
source = "./vpc_module"
vpc_name = "vpc-eu-west-1"
vpc_cidr = "10.80.0.0/16"
providers = {
aws.provider = aws.account_3 # we have to instruct the module what provider to be used
}
}
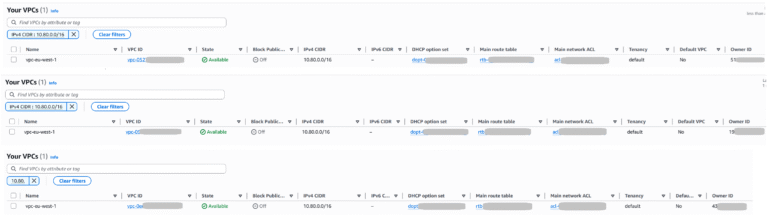
The Result
Let’s check all three AWS Accounts to confirm that VPCs have been created: