SITEMAP
Introduction
Some time ago my colleague Przemek Konitz (https://conix.pl/?p=1784) created a blog article about how to connect 3rd party Azure VNETs with the Aviatrix environment. Recently, I have been asked a similar question but for AWS. The question is: How to connect 3rd party AWS VPC with the existing Aviatrix environment?
It is not possible to just mirror the solution that is used in Azure (the one with Azure VNET Peering between 3rd party VNET and the Aviatrix environment).
The reason is that AWS VPC Peering has limitations that make such a design not possible:
- AWS will drop the packets not destined for Peered VPC
- AWS route next-hop cannot be ENI/instance in another VPC
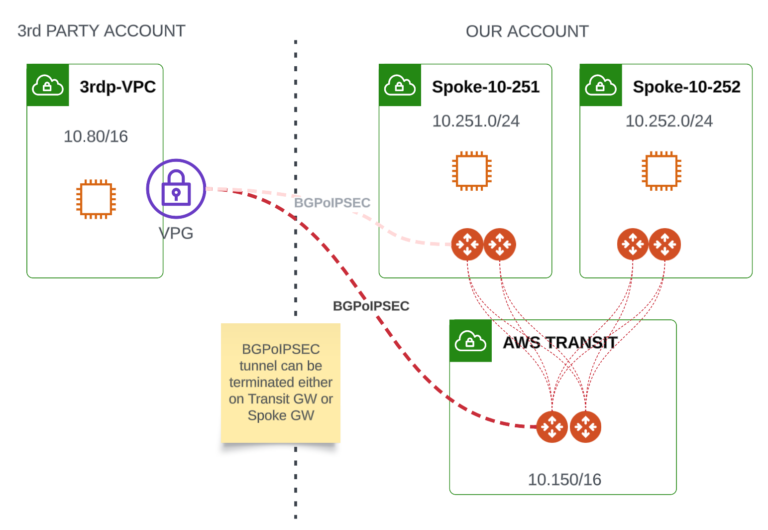
Solution #1 - BGPoIPSEC VPN between 3rd party AWS VPG and Aviatrix Gateway
The BGPoIPSEC tunnel(s) can be built between AWS VPG (deployed in 3rd party’s Account) and Aviatrix Gateway (could be either Transit GW or Spoke GW).
Advantages:
- Access to 3rd party Account is not required
Things to consider:
- 3rd party must deploy a Virtual Private Gateway (VPG) – additional cost (hourly VPN connection price [3rd party Account] + data transfer charges [3rd party Account])
- https://aws.amazon.com/vpn/pricing/ (VPG cost)
- https://aws.amazon.com/ec2/pricing/on-demand/ (data transfer cost)
- Limited throughput because of IPSEC
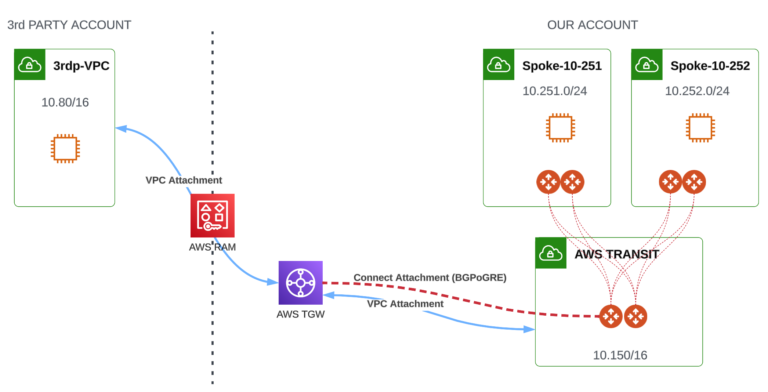
Solution #2 - BGPoGRE between AWS TGW and Aviatrix Gateway
This solution leverages AWS TGW deployed in our Account.
Main characteristics:
- A CONNECT Attachment will be built on top of the underlay VPC Attachment (quite a complicated design).
- BGP will be built on top of the GRE.
- Aviatrix TGW-O is not used.
Advantages:
- Throughput is not limited. AWS underlay will be used
- BGP connection will be visible in Aviatrix CoPilot
- Access to 3rd party Account is not required
Things to consider:
- AWS TGW will be used – additional cost
- TGW VPC attachment per hour [VPC owners – 3rd party Account + and our Account] + data transfer charges [TGW owner – our Account] + TGW Connect attachment [TGW owner – our Account])
- https://aws.amazon.com/transit-gateway/pricing/
- AWS TGW will not be visible in Aviatrix CoPilot
- AWS TGW is not orchestrated by Aviatrix Controller
- AWS TGW Routing must be created “manually” (AWS Console or TF Code)
- AWS TGW Attachment will be shared (using AWS RAM service) with 3rd party Account (no additional cost)
- CIDR and ASN must be assigned to AWS TGW
Note: there is also another “version” of this integration.
The BGPoIPSEC could be used. There will be no VPC-Attachment and Connect Attachment with Aviatrix Transit in such a case.
Instead, the TGW VPN Attachment could be used to create BGPoISPEC tunnels.
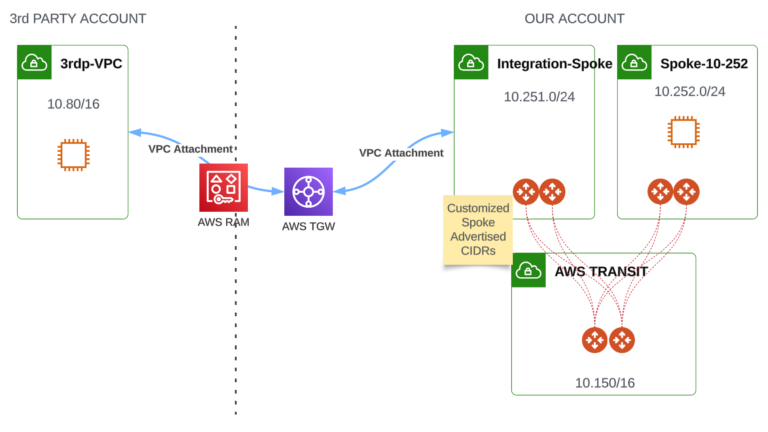
Solution #3 - AWS TGW VPC Attachment with 3rd party VPC
This solution leverages AWS TGW deployed in our Account (similarly to option #2).
Aviatrix TGW-O is not used.
There will be a Route configured in Integration-Spoke Subnets RTs pointing towards 3rdp-VPC (with nh = tgw-attachment)
Advantages:
- Throughput is not limited. AWS underlay will be used
- It is not required to onboard the 3rd party Account to the Aviatrix Controller
- Full control of 3rdp party CIDRs advertised from Integration-Spoke to Transit (“Customized Spoke Advertised CIDRs” feature can be used)
Things to consider:
- AWS TGW will be used – additional cost
- TGW VPC attachment per hour [VPC owners – 3rd party Account and our Account] + data transfer charges [TGW owner – our Account])
- https://aws.amazon.com/transit-gateway/pricing/
- AWS TGW will not be visible in Aviatrix CoPilot
- AWS TGW is not orchestrated by Aviatrix Controller
- AWS TGW Routing created “manually” (AWS Console or TF Code)
- AWS TGW Attachment will be shared (using AWS RAM service) with 3rd party Account (no additional cost)
Details of this solution, incl. Terraform code: https://cloud-cod.com/index.php/2024/01/09/aws-tgw-vpc-attachment-with-3rd-party-vpc-using-aws-ram/
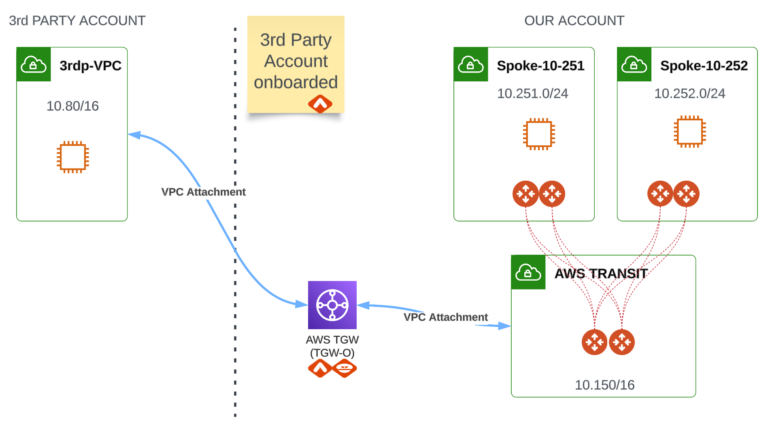
Solution #4 - Aviatrix Orchestrated AWS TGW VPC Attachment with 3rd party VPC
This solution is a “better version” of solution #3. The beauty of it is that the creation/management/maintenance of AWS TGW, VPC Attachment, Routing, Policies is orchestrated by Aviatrix Controller.
This solution leverages AWS TGW deployed in our Account (similarly to option #3) but the AWS TGW will be built through Aviatrix Controller.
The 3rd party Account must be onboarded to the Aviatrix Controller to orchestrate the attachment.
Aviatrix TGW-O can be used. As already stated, it gives full AWS TGW visibility in CoPilot and full AWS TGW Orchestration done by Aviatrix Controller when it comes to TGW Attachments, Routes, Policies, etc.
Advantages:
- Throughput is not limited. AWS underlay will be used
- AWS TGW orchestrated by Aviatrix Controller
- AWS TGW visible in CoPilot
- AWS TGW Attachment sharing is not required (AWS RAM) because the 3rd party Account is onboarded
Things to consider:
- AWS TGW will be used – additional cost (TGW VPC attachment per hour [VPC owners – 3rd party Account and our Account] + data transfer charges [TGW owner – our Account])
- https://aws.amazon.com/transit-gateway/pricing/
- The 3rd party Account must be onboarded to Aviatrix Controller (either using Access Key Credentials or IAM Roles)
Details of this solution, incl. Terraform code: https://cloud-cod.com/index.php/2023/12/27/aviatrix-orchestrated-aws-tgw-vpc-attachment-with-3rd-party-vpc/