SITEMAP
Introduction
My previous blog article (https://cloud-cod.com/index.php/2023/12/06/connecting-3rd-party-aws-vpcs-with-aviatrix-environment/) presented a few options for connecting 3rd party AWS VPCs to your Aviatrix environment.
This post deep dives into solution #4 – “Connecting 3rd party AWS VPCs with Aviatrix environment”. I will show you how to configure this type of integration using Terraform.
Initial setup
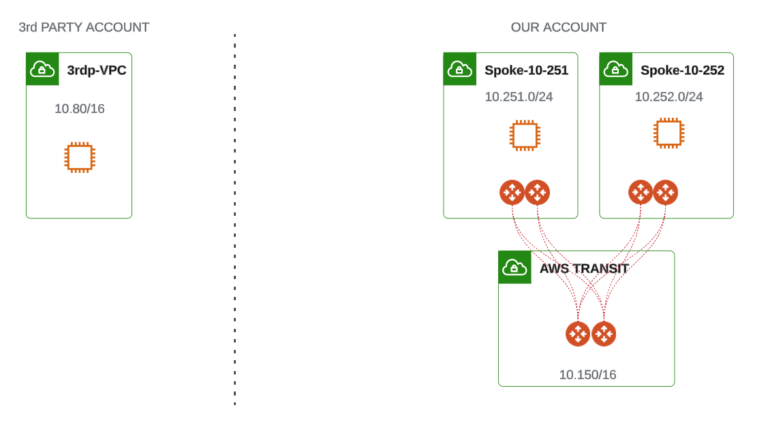
Let’s keep our test environment very simple. Your real PROD environment would be of course much more sophisticated. My test environment consists of the following:
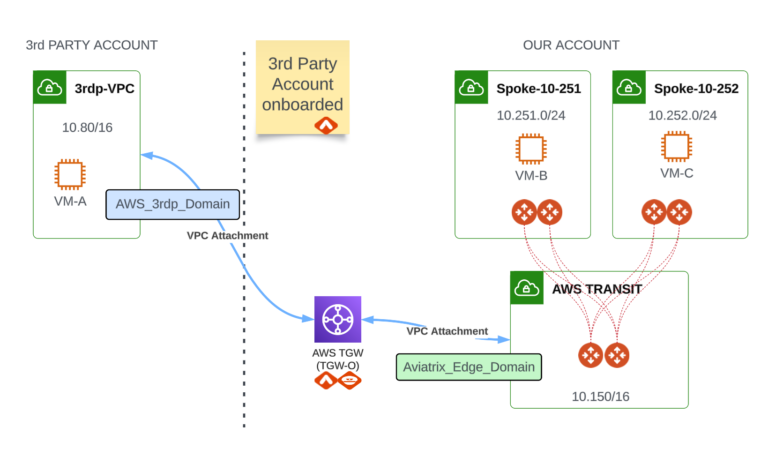
- one Aviatrix Transit VPC (10.150.0.0/16)
- two Spoke VPCs (10.251.0.0/24 and 10.252.0.0/24) connected to Transit VPC through Aviatrix Spoke Gateways.
I used the following modules to set up the environment:
There is also one VPC (10.80.0.0/16) that does not belong to our organization (Account) and is out of our control (this is a 3rd party VPC). Please keep in mind that with this solution the 3rd party Account must be onboarded to Aviatrix Controller (either using Access Key Credentials or IAM Roles)
What is more, I have deployed test VMs in 3rd party VPC and both Spoke VPCs that will help us with a test scenario later.
Test Scenario Diagram
The goal is to achieve a connectivity between VM-A in 3rd party VPC and VM-B (and VM-C) in Spoke VPCs connected to Aviatrix Transit.
Configuration of AWS TGW and its Attachments
AWS Transit Gateway creation
Let’s create AWS Transit Gateway (AWS TGW). However, instead of using aws_ec2_transit_gateway, we are going to use a dedicated Aviatrix resource. Please also notice that AWS TGW will be created in the Account owned and controlled by us.
Why are we using Aviatrix resource? The reason: we want to leverage the AWS TGW Orchestrator feature (more details later) provided by Aviatrix.
resource "aviatrix_aws_tgw" "test_aws_tgw" {
account_name = "AWS-Jakub-2"
aws_side_as_number = "65009"
region = "eu-central-1"
tgw_name = "avtx-euw-tgw"
}
AWS-Jakub-2 is a name of my AWS Account onboarded to Aviatrix Controller.
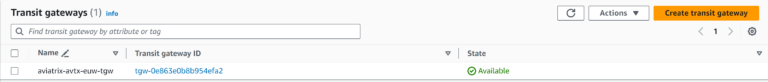
AWS TGW has been created:
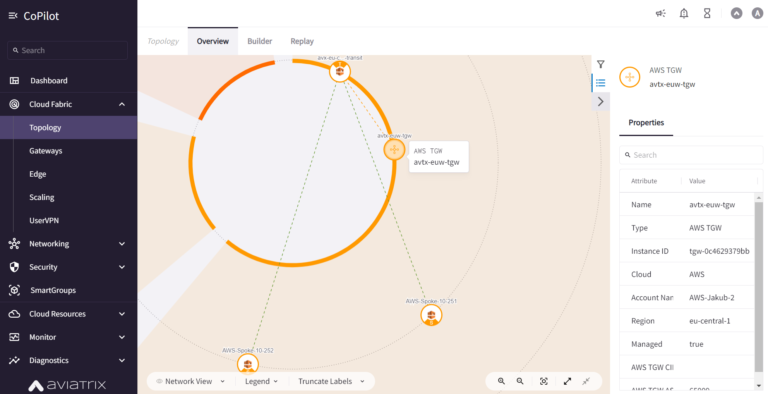
Now, we can check how it looks in Aviatrix CoPilot as well. Go to Networking > Connectivity > AWS TGW:
AWS TGW Network Domains creation
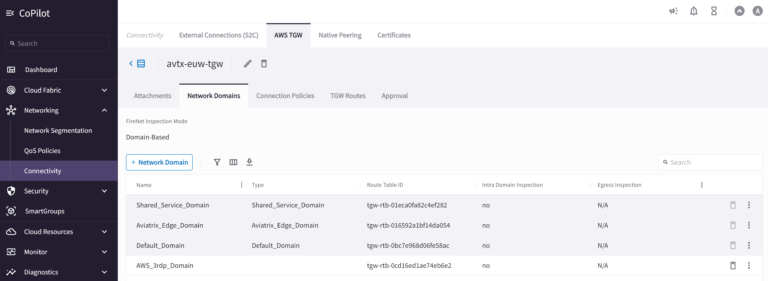
In our lab, we will use a few Network Domains, that will help us with controlling and securing communication flows between environments. Let’s create 3 (default, shared_service, and edge) Network Domains (using Aviatrix TGW-Orchestrator resources of course):
# Create Network Domains
resource "aviatrix_aws_tgw_network_domain" "Default_Domain" {
name = "Default_Domain"
tgw_name = aviatrix_aws_tgw.test_aws_tgw.id
}
resource "aviatrix_aws_tgw_network_domain" "Shared_Service_Domain" {
name = "Shared_Service_Domain"
tgw_name = aviatrix_aws_tgw.test_aws_tgw.id
}
resource "aviatrix_aws_tgw_network_domain" "Aviatrix_Edge_Domain" {
name = "Aviatrix_Edge_Domain"
tgw_name = aviatrix_aws_tgw.test_aws_tgw.id
}
We can verify the newly created Network Domains in the Aviatrix CoPiliot. Go to Networking > Connectivity > AWS TGW > Network Domains:
Please notice that there is a dedicated AWS TGW Route Table per Network Domain created by the Aviatrix Controller.
Attaching Aviatrix Transit to AWS TGW
The Aviatrix Transit VPC will be connected to AWS TGW using a VPC Attachment. In this case, we are also going to use a dedicated Aviatrix resource (which is part of AWS TGW-Orchestrator feature).
# Attach Aviatrix TrGW to AWS TGW
# hybrid_connection must be enabled on Aviatrix TrGW
resource "aviatrix_aws_tgw_transit_gateway_attachment" "test_transit_gateway_attachment" {
tgw_name = aviatrix_aws_tgw.test_aws_tgw.tgw_name
region = "eu-central-1"
vpc_account_name = "AWS-Jakub-2"
vpc_id = module.mc_transit_aws.transit_gateway.vpc_id
transit_gateway_name = module.mc_transit_aws.transit_gateway.gw_name
}
To verify that the Attachment has been created go to Networking > Connectivity > AWS TGW > Attachments > Transit Gateway.
Please notice that the AWS TGW Attachment with Aviatrix Transit VPC is placed in Network Domain “Aviatrix_Edge_Domain”.
Wta is also great is that you can see your AWS TGW in the CoPilot Topology View (Cloud Fabric > Topology):
Attaching 3rd party VPC to AWS TGW
Now, let’s attach 3rd party VPC to AWS TGW. The 3rd party VPC’s Account must be onboarded to the Aviatrix Controller.
Additionally, we will create a new Network Domain called “AWS_3rdp_domain” and it will be used by our 3rd party spoke VPC.
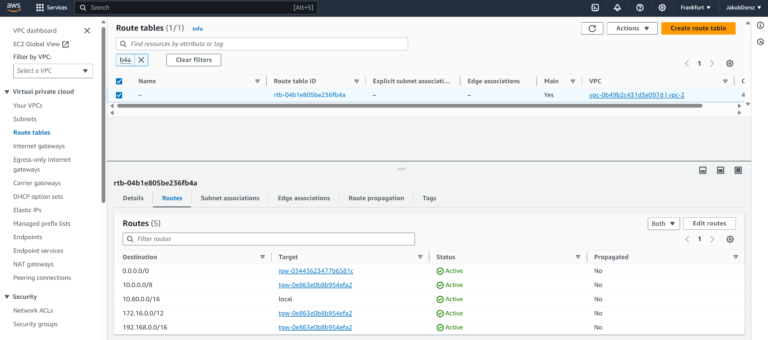
Warning: there must be no RFC1918 routes (10/8, 172.16/12, 192.178/16) in 3rd party VPC Subnets Route Table.
resource "aviatrix_aws_tgw_network_domain" "AWS_3rdp_Domain" {
name = "AWS_3rdp_Domain"
tgw_name = aviatrix_aws_tgw.test_aws_tgw.id
}
# Attachment to Spoke VPC (3rd party Account must be onboarded)
resource "aviatrix_aws_tgw_vpc_attachment" "avx_aws_tgw_3rdp_vpc_att" {
tgw_name = aviatrix_aws_tgw.test_aws_tgw.tgw_name
region = "eu-central-1"
network_domain_name = "AWS_3rdp_Domain"
vpc_account_name = "Jakub-Private" # 3rd party Account name as known by Aviatrix Controller
vpc_id = "vpc-0b49b2c431d3e097d" # id of 3rd party spoke vpc
}
Go to Networking > Connectivity > AWS TGW > Attachments > VPC:
Go to Networking > Connectivity > AWS TGW > Network Domains:
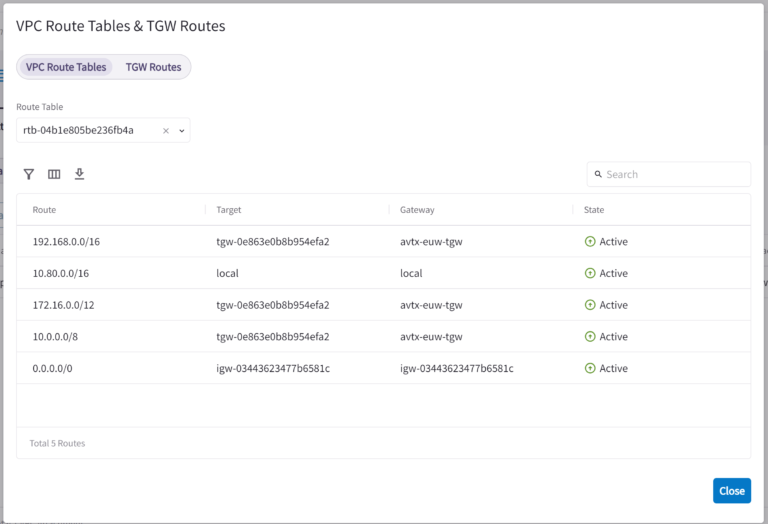
There have been some additional activities performed in the background by the Aviatrix Controller in “spoke” 3rd party VPC. Namely, the Aviatrix Controller automatically inserted RFC1918 routes towards AWS TGW. AWS TGW Orchestrator works! No more adding Routes manually!
Of course, we do not have to use AWS Management Console to check this kind of information. All the necessary details are already present in the Aviatrix CoPilot. Go to Networking > Connectivity > AWS TGW > Attachments > VPC > View VPC Route Tables & TGW Routes:
Verification and Tests
Let’s summarize what has been deployed already:
- AWS TGW using Aviatrix resource (because we want to leverage AWS TGW Orchestrator feature)
- Attachment between AWS TGW and Aviatrix Transit
- VPC attachment between AWS TGW and AWS “spoke” 3rd party VPC
- the “spoke” 3rd party VPC has been assigned to Network Domain “AWS_3rdp_Domain”
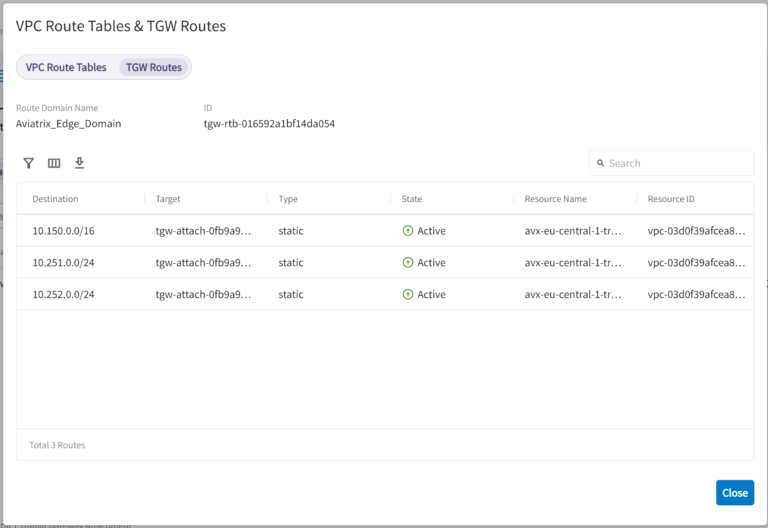
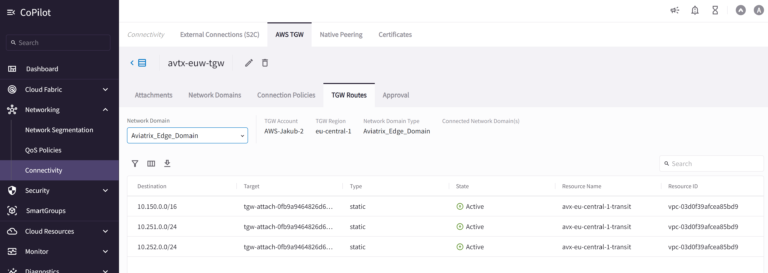
Let’s verify AWS TGW Route Table. Go to Networking > Connectivity > AWS TGW > Attachments > Transit Gateway > View VPC Route Tables & TGW Routes:
As we can see AWS TGW Route Table of Aviatrix_Edge_Domain knows not only the “spoke” 3rd party VPC CIDR but also both Aviatrix Spoke VPCs connected to Aviatrix Transit!
The same can be checked in Networking > Connectivity > AWS TGW > TGW Routes. Please select “Aviatrix_Edge_Domain” from the dropdown Network Domains list.
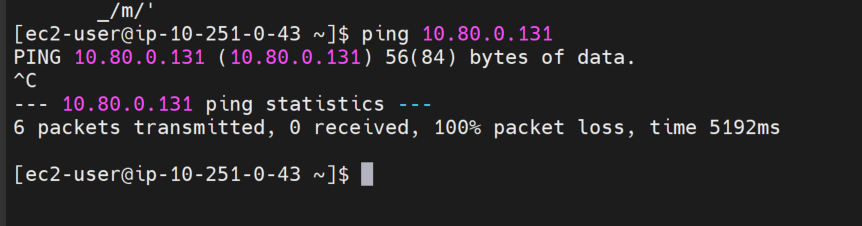
Will the connectivity between VM-A (10.80.0.131 is an IP address of VM-A) in 3rd party “spoke” VPC and VM-B (or VM-C) work? The answer is.. NO.
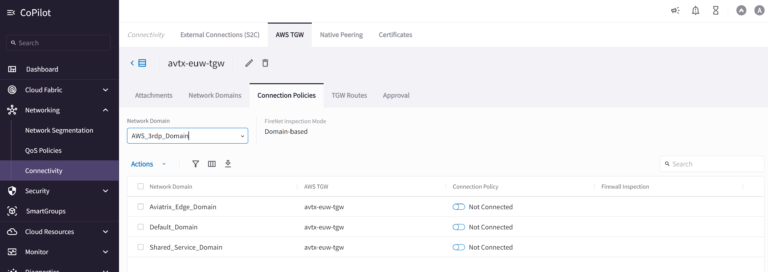
Why? Please take a look at the Connection Policies in the Aviatrix CoPilot. Go to Networking > Connectivity > AWS TGW > Connection Policies. Please select AWS_3rdp_Domain from the network Domain list. There is no Connection Policy in place allowing communication between Aviatrix_Edge_Domain and AWS_3rdp_Domain. Zero-trust first! We must enable it!
We can set a Connection Policy between Network Domains using Terraform code as shown below:
# Connection Policy
resource "aviatrix_aws_tgw_peering_domain_conn" "aws_tgw_peering_domain_conn_1" {
tgw_name1 = "avtx-euw-tgw"
domain_name1 = "AWS_3rdp_Domain"
tgw_name2 = "avtx-euw-tgw"
domain_name2 = "Aviatrix_Edge_Domain"
}
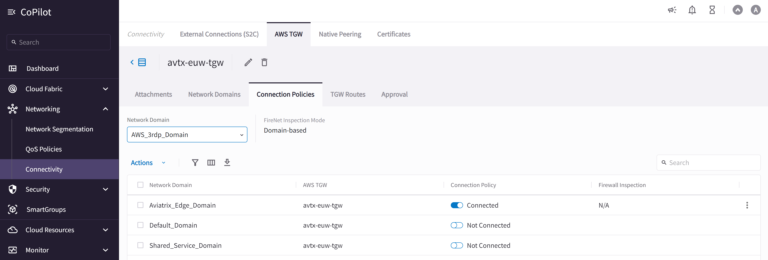
Let’s verify in the Aviatrix CoPilot that the Connection Policy now allows communication between our two Network Domains. Go to Networking > Connectivity > AWS TGW > Connection Policies. Please select AWS_3rdp_Domain from the network Domain list.
Verify that PING from VM-B towards VM-A (10.80.0.131) is now working.
Of course, we can see this traffic (our PING packets) in Aviatrix CoPilot. Please go to Monitor > Flow IQ > Records:
Summary
I have presented an easy way of connecting 3rd party VPCs with your Aviatrix environment. There are plenty of benefits to this approach. The main ones I could think of are:
- no need for manual creation of resources (incl. AWS Spoke VPC Routes) -> AWS TGW Orchestrator does it all for you
- AWS TGW visibility in Aviatrix CoPilot, incl. all Routes, Connection Policies, and more.
More information about AWS TGW Orchestrator can be found at Aviatrix Documentaion: https://docs.aviatrix.com/documentation/latest/building-your-network/tgw-landing-page.html?expand=true